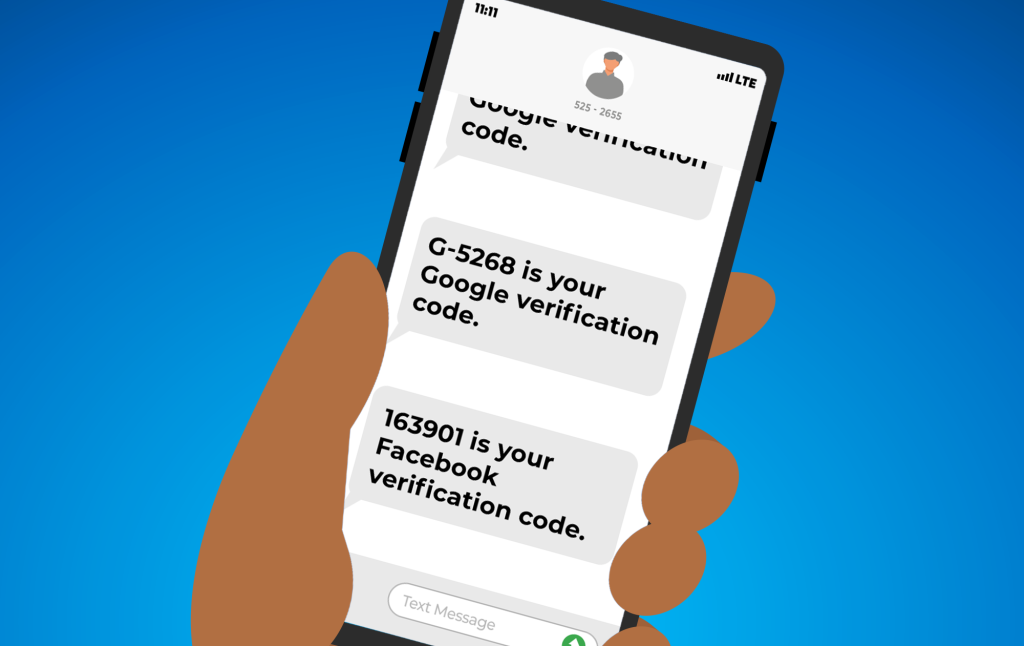
We've all had those moments of confusion when our phone buzzes with a notification that doesn't seem quite right. If you've ever woken up to a text with some random numbers and wondered what it is, you're not alone.
Getting a code for two-factor authentication (2FA) from a service you use when you didn't request one deserves some attention. Rather than ignoring the strange message, it's a good idea to take action to help protect your online accounts.
Understanding 2FA
2FA, or "Two-Factor Authentication," is an important security feature many apps and websites use. It adds an extra verification step beyond just a password. After you log in, 2FA will text or email you a special code to enter before you're given access to your account. This acts like a second lock, keeping hackers out even if they somehow steal your password.
Spot the Warning Signs
When you receive a 2FA code you didn't request, it's a clear sign that someone is trying to access one of your online accounts. It often indicates that your password has been compromised through a large-scale data breach or a more targeted attack. Hackers may be attempting to log in using your stolen credentials, and the 2FA code is the only thing standing in their way.
Taking Immediate Action
Rather than ignoring the 2FA code or brushing it off, it's important to take action right away to secure your accounts.
- Do not click on any links in the email or SMS. Open a browser, log in to the relevant account, and change your password to something unique and complex. Make sure it's different from the one you used before and not used for other accounts.
- Check if your old password was involved in any known breaches using a tool such as HaveIBeenPwned.com. This can help you identify if you have any other accounts that may be at risk.
- Consider changing passwords for any other accounts using the same or similar passwords in case of credential stuffing attacks. This is when hackers use stolen passwords from one breach to try and access other accounts.
- Be wary of emails or texts asking you to provide a 2FA code. Legitimate services will never ask for this, and it's likely a phishing attempt.
This unexpected 2FA code experience is a valuable reminder of the importance of proactive security measures. Two-factor authentication is what saved you this time by blocking the hacker's attempt to access your account, so take a moment to ensure you've enabled it on every site that offers it.
Additionally, using unique, strong passwords for each account is essential to prevent the ripple effects of a single data breach. A password manager can help you generate and store complex credentials, ensuring one compromised password doesn't put all your other accounts at risk.
While complete online security can never be guaranteed, taking these fundamental steps - enabling 2FA and using unique passwords - goes a long way toward safeguarding your personal information and digital identity.
Jim's IT Services in Australia
For a free quote please follow the below steps


Have you used Jim's before?

-
Police Checked
A police check is issued as an official document to verify a background check by police or government agency to enumerate any criminal records a service provider may have.
-
$1,000,000 Work Guarantee
This guarantee is up to one million dollars for work done by Jim's Group Franchisees.
If you are not satisfied with the job, we will inspect it and have any problems fixed. If we believe the job is good and you do not, we will jointly agree on an independent expert to provide a report at our expense, and fix any problems found. Until this is done, you need not pay for the job. If problems are not fixed within a fortnight, any advance will be refunded.
Only if no problems are found by the expert, will you be asked to pay the agreed price for the job and half the cost of the report.
If the job is done to get your bond back on leaving a rental property, the job is only considered good when the agent or landlord is satisfied.
If payment is made in advance and the job not done, the payment will be refunded. -
$10,000,000 Public
Liability
A public liability policy covers damage to people or property.
It is in place to protect business owners if someone sues for personal injury or damage to property.